You may need to provide access to applications to users in a different Okta organization. This method utilizes the Okta Org2Org application with SAML 2.0, and Dropbox Business as an example.
Navigate to Applications, Browse App Catalog, search for Dropbox Business, and add the integration. From there, return to Applications and select Dropbox Business to initiate the configuration. In the General tab, enter a name for the application and save. Next, go to the Sign-on tab and retrieve the Sign-on URL and the Signing Certificate to configure Dropbox.
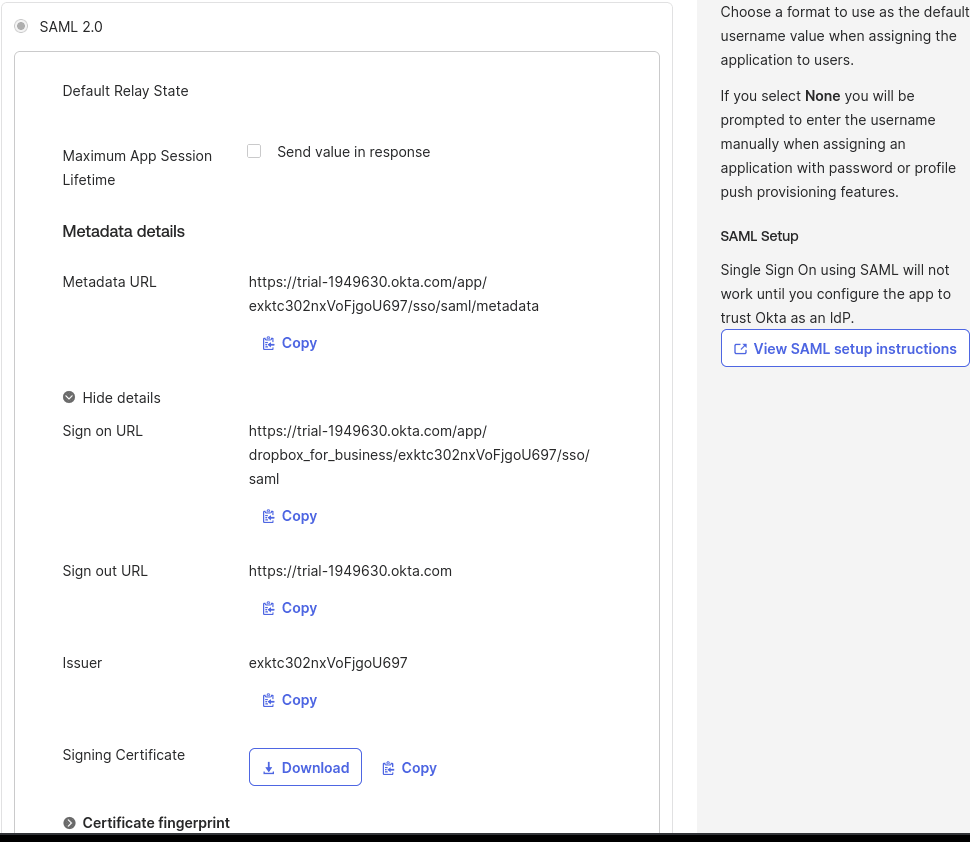
Sign in to the Dropbox Admin console and go to the security tab to update the certificate and paste the sign-in URL.
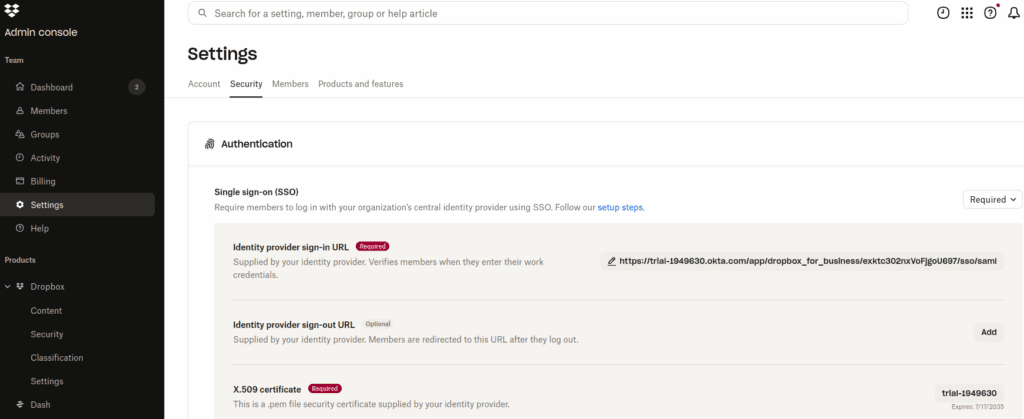
In Okta, review the advanced sign-on settings, as well as the settings for silent provisioning and credential details. You’ll likely want silent provisioning enabled, and the Okta username and Create and Update selected. On the provisioning tab, select ‘To App‘ and enable the ‘Create User’, ‘Update Attributes’, and ‘Deactivate Users’ options.
You can verify Dropbox account provisioning by going to the assignments tab and assigning a user or group. Log in as your test user and click the Dropbox tile on the end user dashboard.
To allow users from another organization to use the Dropbox app, you have to configure an identity provider. The tenant that hosts the Dropbox application (Service Provider) needs to create a trust relationship with the organization that manages the identities (IdP). Go to Security, then Identity Providers, select SAML 2.0 from the list, and click Next.
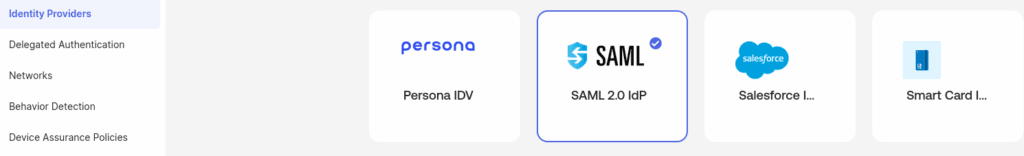
The next step requires information from the identity provider. Log in to that tenant and install the Okta Org2Org application. Go to Applications, then Browse Application Catalog, search for “org2org,” and add the integration. The Org2Org application requires a Base URL, which is the address of the Service Provider.
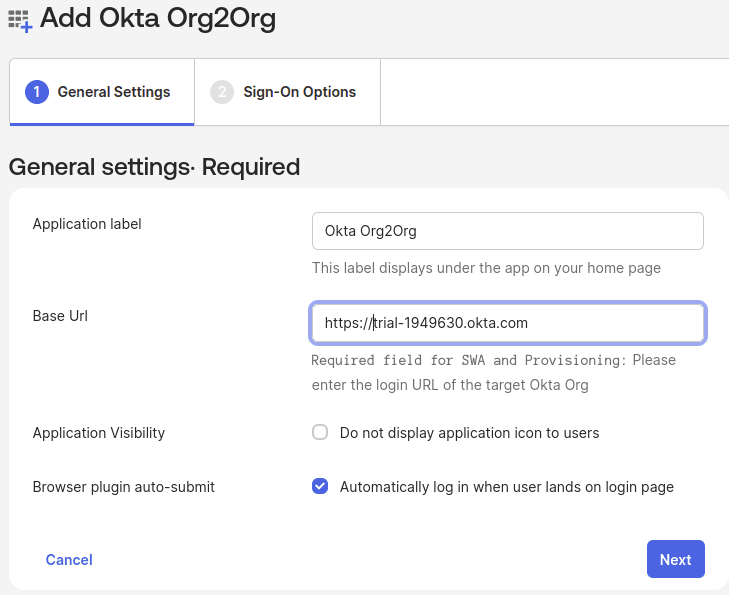
On the next screen, click More Details to view the Issuer URI, Sign-on URL, and download the Signature Certificate. This information is used in the SAML 2.0 configuration back on the Service Provider. My configuration for the SAML 2.0 settings is:
Click finish to view the Assertion Consumer Service URL and Audience URI and configure them in the Okta Org2Org app on the Identity Provider.
Next, we need to configure provisioning so that user states get synced to the Service Provider. Obtain an API key from the Service Provider by navigating to Security, then API, and then Tokens. Create a token and copy it into the Okta Org2Org settings under Provisioning and Integration.
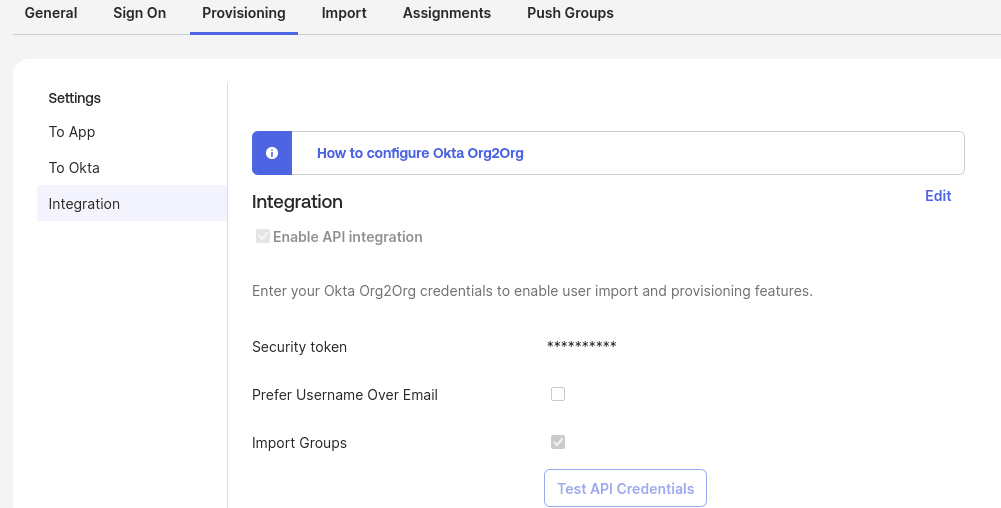
Next, navigate to “To App” and enable Create Users, Update User Attributes, and Deactivate Users. Finally, go into the Assignments tab and assign a user or group to Okta Org2Org. Log in as that user and click the Org2Org tile on their user dashboard to verify provisioning at the Service Provider. Assuming that worked, assign that user (or group) to the Dropbox Business application over on the Service Provider.
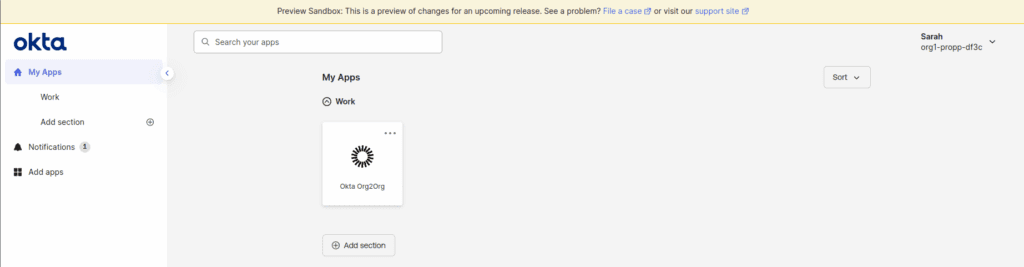
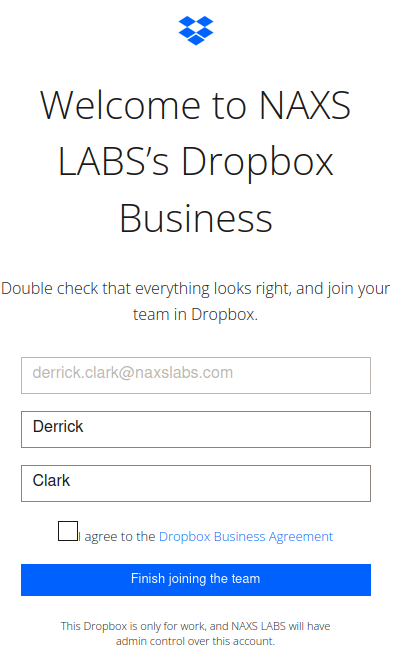
In this scenario, Sarah logs in to her user dashboard at Org1, which serves as the Identity Provider. Once there, she clicks on the Okta Org2Org tile and is directed to the Service Provider’s login page, where she will enroll in any required authenticators.
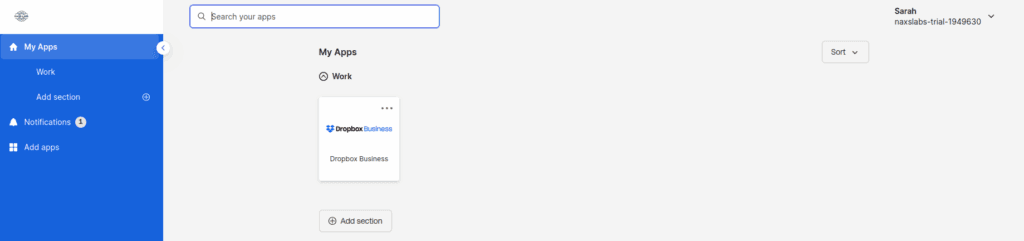
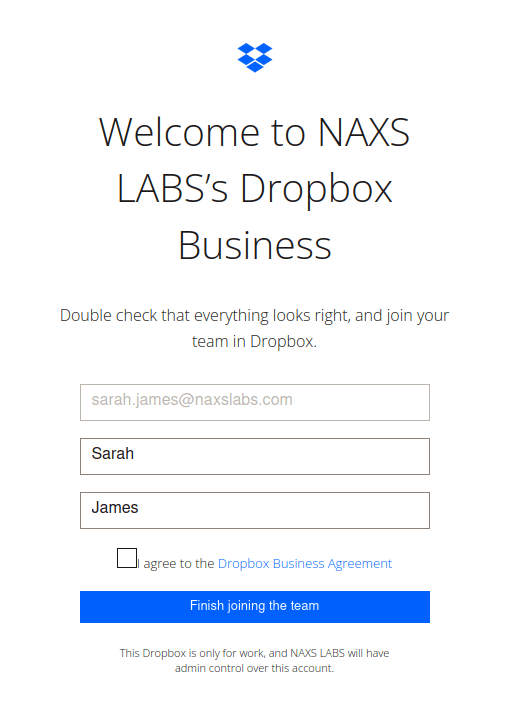
Once she’s logged into the Service Provider, Sarah clicks the Box Business tile and joins the Dropbox Team. There are a few first-time confirmations that she has to go through, but she eventually gets signed into Dropbox.
© NAXS Labs All Rights Reserved